Data confidence, integrity, nonrepudiation, identity and access control are the five key factors to protect online bank, stock, tax from attacks.
数据机密性、完整性、防抵赖、身份识别、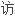

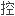 制五个关键
制五个关键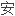 全
全 题是保
题是保

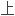 银行、
银行、
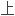
 券、
券、
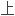 报税等典型的
报税等典型的
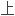 交易系统
交易系统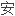 全运行的基础。
全运行的基础。
声明:以上例句、词性分类均由互联网资源自动生成,部分未经过人工审核,其表达内容亦不代表本软件的观点;若发现问题,欢迎向我们指正。